Building A Password Cracker in AWS
Getting Started
It may seem obvious, but first you'll need an active AWS account. You can register for an account here if you don't already have one. Once you have an account, there's one more housekeeping step to take. GPU-backed instances at AWS (in our case, we'll be using one of the P3 type instances), require AWS to allocate an allotment of vCPUs to your account that can be used for launching these instances. So, we'll need to request a limit increase from the default 0 to 32 in order to launch a p3.8xlarge instance. You can request limit increases in AWS on the My Service Quotas page. Refer to our video walkthrough (3:05).
Once your account has been allocated vCPUs, you can now launch a p3.8xlarge instance. Be forewarned, these instances will cost you almost $9,000 dollars if you run it continuously for a month. Do Not Forget To Power This Off when it is not in use. Here are a few other options for GPU-backed systems to consider as well, though from testing and analysis, we've found the 8xlarge to be the best blend of performance and cost.
P3 Instance Types
Configuring Your Instance
Once your account is approved you can now launch your instance (3:40). Here are the basic requirements for your instance:
Use AMI: ami-0817d428a6fb68645
Provision at least 250gb of storage (cracking files take up lots of room)
Optional: Use security groups to restrict access (e.g., ssh) from only desired locations
After the instance is launched we need to run a few commands:
sudo apt update #collect package updatessudo apt upgrade #install package updatessudo apt-get install -y build-essential linux-headers-$(uname -r) p7zip-full linux-image-extra-virtual #install additional packages
Now we need to edit a configuration file, so run:sudo [your fav editor] /etc/modprobe.d/blacklist-nouveau.confand add the following lines:
blacklist nouveau
blacklist lbm-nouveau
options nouveau modeset=0
alias nouveau off
alias lbm-nouveau off
A few more commands:
sudo echo options nouveau modeset=0 | sudo tee -a /etc/modprobe.d/nouveau-kms.confsudo update-initramfs -usudo reboot
Configuring Your GPUs
Now we need to download and install our GPU Drivers and SDKs (7:18). Download and install NVIDIA Drivers:
wget https://us.download.nvidia.com/tesla/450.80.02/NVIDIA-Linux-x86_64-450.80.02.run #downloadsudo bash NVIDIA-Linux-x86_64-450.80.02.run #install, accept all defaults
Download and install Cuda Developer's Kit:
wget https://developer.download.nvidia.com/compute/cuda/11.1.0/local_installers/cuda_11.1.0_455.23.05_linux.run #downloadsudo bash cuda_11.1.0_455.23.05_linux.run #install, accept all defaults
Pro tip: Save the Cuda download somewhere. If you ever turn your cracker off and get errors running hashcat when you turn it back on, re-run the install line. We think AWS sometimes refreshes the drivers or something and hashcat doesn't like it very much.
Download and Run Hashcat
We're almost there! Just quick install of 7zip and a download of hashcat and we're off and running (8:30). Download 7zip:
sudo apt install p7zip-full
The video has a typo on this line (missing the "p")
To make it easy, here are the remaining lines of code. You can run each one-at-a-time or copy and paste the whole block into the terminal:
sudo cd /opt #move into /opt, this is personal preference, I just keep everything here to make it easy for us
sudo wget https://hashcat.net/files/hashcat-6.1.1.7z #download hashcat
sudo 7z x hashcat-6.1.1.7z #extract hashcat
sudo mv hashcat-6.1.1.7z hashcat #change directory name to just hashcat
sudo cd hashcat #move into hashcat directory
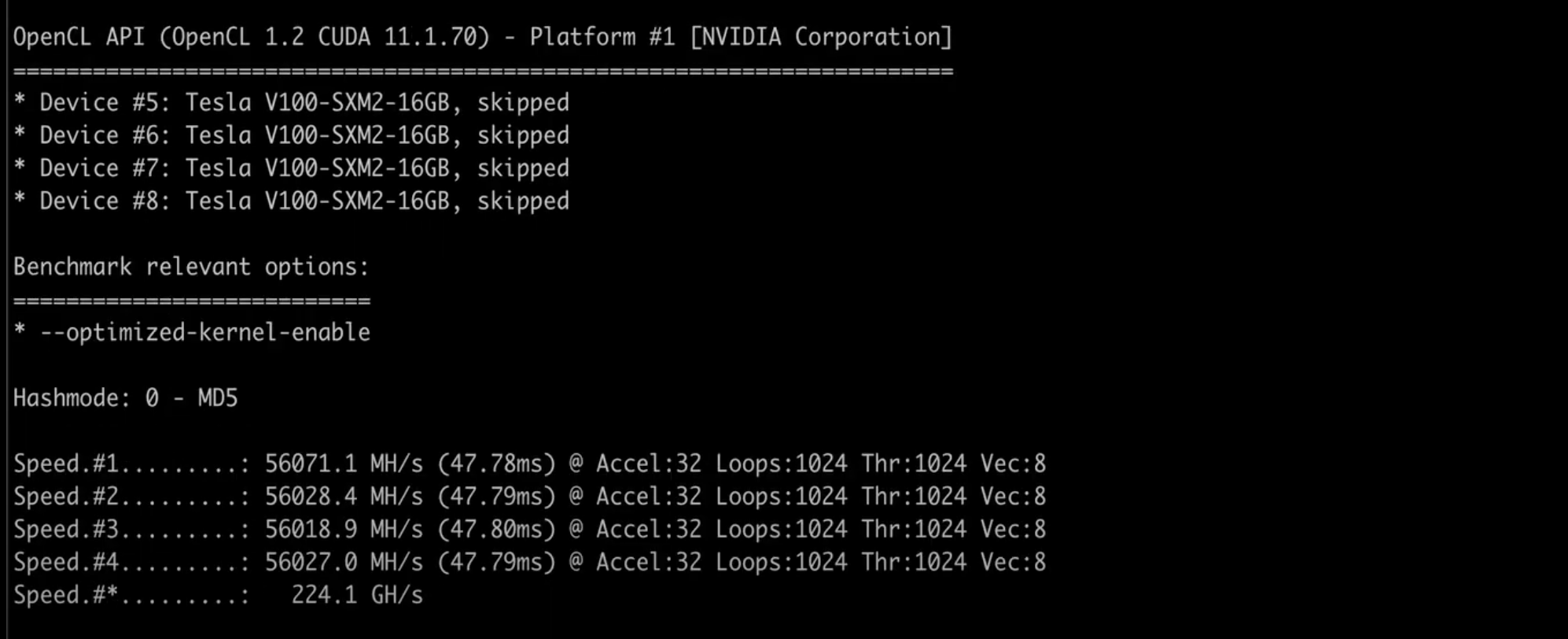
sudo ./hashcat.bin -b #run hashcat in benchmark modeHashcat Running in Benchmark Mode
Wrapping Up
Congratulations, if all went well, you should have a working password cracker in AWS. From here, you'll need to get yourself a few wordlists, rules, masks, and of course—some [legally obtained] hashes to crack. If you liked this post and want to see a video on cracking techniques or tips and tricks, comment in the YouTube comment section.
There is also a great cracking guide available on Amazon that contains lots of examples, rules and dictionary sources. Hash Crack: Password Cracking Manual